FlareOn-9 Writeups 10 Nur Getraumt

Introduction
Description:
This challenge is a Macintosh disk image (Disk Copy 4.2 format, for those who need to know) containing a 68K Macintosh program. You must determine the passphrase used to decode the flag contained within the application. Super ResEdit, an augmented version of Apple’s ResEdit resource editor which adds a disassembler, is also included on the disk image to help you complete the challenge, though you will likely also need to do some outside research to guess the passphrase. This application can be run on any Macintosh emulator (or any real Macintosh from as far back as a Mac Plus running System 6.0.x up to a G5 running Classic). The setup of the emulation environment is part of the challenge, so few spoilers live here, but if you want to save yourself some headaches, Mini vMac is a pretty good choice that doesn’t take much effort to get up and running compared to some other options. This application was written on a Power Macintosh 7300 using CodeWarrior Pro 5, ResEdit, and Resourcerer (my old setup from roughly 1997, still alive!). It was tested on a great many machines and emulators, and validated to run well on Mac OS from 6.0.8 through 10.4. Happy solving! Be curious!
Time for some research on the hardware we need to emulate :D.
The Power Macintosh 7300 is a computer from 1997 that have 16MB of RAM and a PowerPC 604e CPU:

The simple fact of writing this sentence is funny, as I was not even born when this big boy came out.
The PowerPC 604e processor is operating between 166 and 233 MHz, and as the name imply, support the PowerPC instruction set.
Another small detail: the provided .img file seems to be a copy of a floppy disk, so wouldn’t be able to mount it anywhere for now.
Emulator Setup
As the description suggest using the Mini vMac emulator, we’ll try to go with that.
First thing first, we need to find a ROM for the Power Macintosh 7300. As Apple obviously does not allow the download of such ROM, we have to find it by ourselves. Thanks to the Internet Archive, we can download a set of old Macintosh ROM, including the Power Mac 7300.
We can test the ROM by launching the emulator with it:
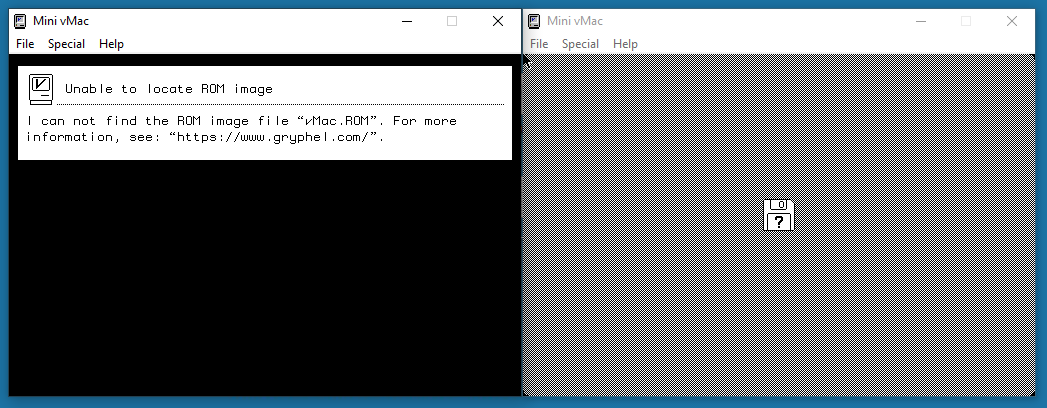
On the left, the state of the emulator without any ROM image, and on the right, the default screen telling us that no operating system have been found.
The next step is to install the operating system in the emulator. We’ll choose System 6, available on the official Apple website. The download comes in two files (the two floppy disks): disk 1 and disk 2.
Finally, we’ll need a set of blank disks to perform the actual installation.
After unzipping the two System 6 disks, we have to plug the first one, “System Startup”, in the emulator.
The “System Startup” disk contains the binaries needed to perform the actual install:
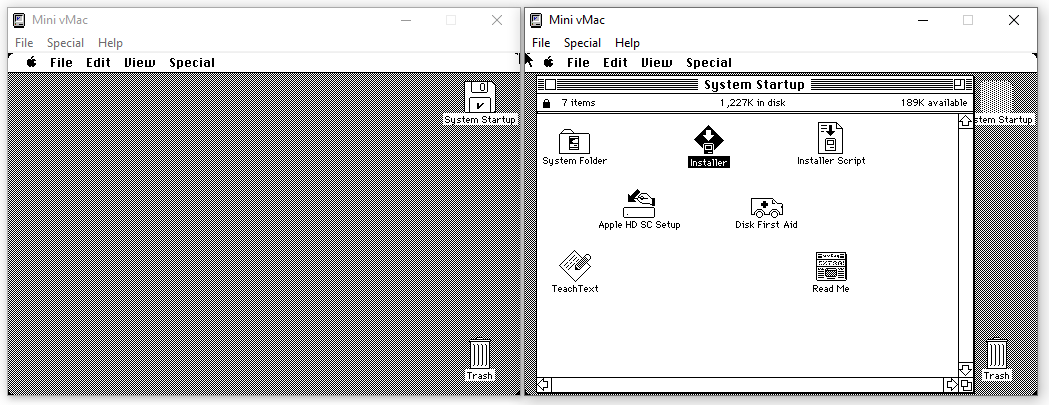
Before starting the installation, we have to plug one of the blank floppy disk image in the emulator. We’ll use the 024M.dsk one:
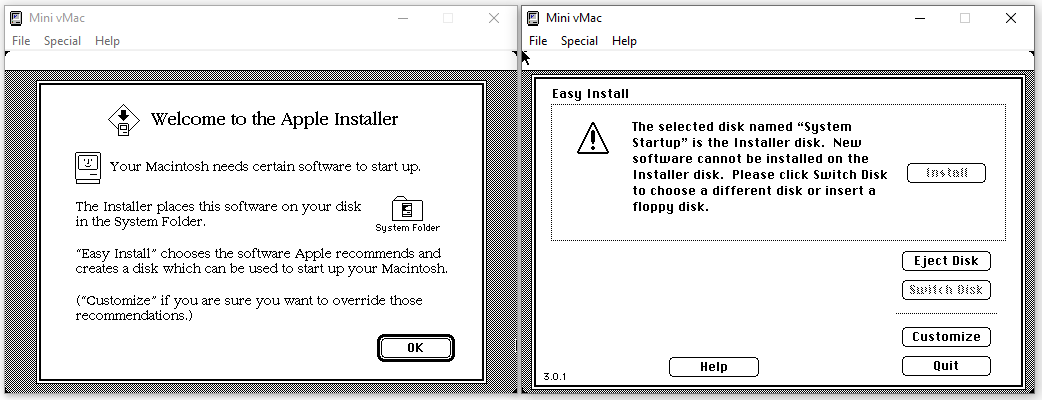
With the empty disk being detected, we can launch the System 6 installation:
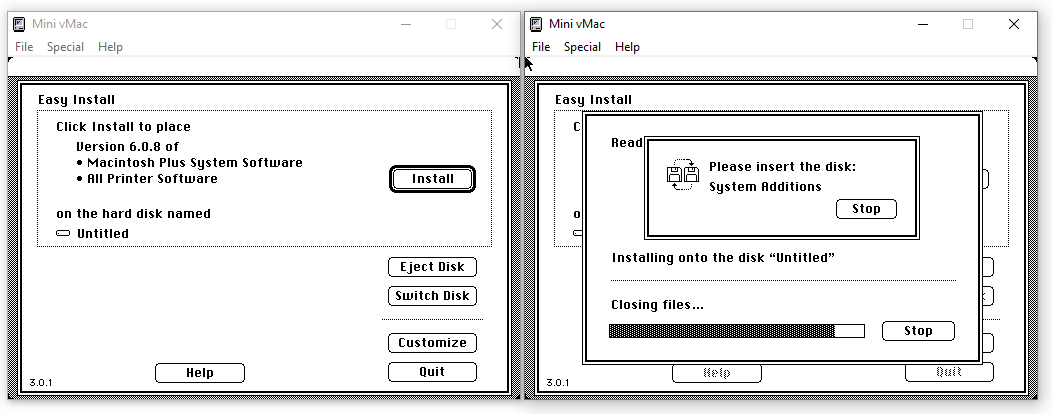
When asking, the second floppy disk image, “System Additions”, need to be inserted into the emulator. After a few seconds of waiting, System 6 is installed, and we can reboot the emulator to start using our new operating system:
Binary Overview
After booting the emulator, we can insert the provided .img floppy disk image to access the challenge, along with the provided disassembler.
First, let’s open-up the target binary. A password is required to get the flag. With a dummy input, the displayed flag is gibberish:
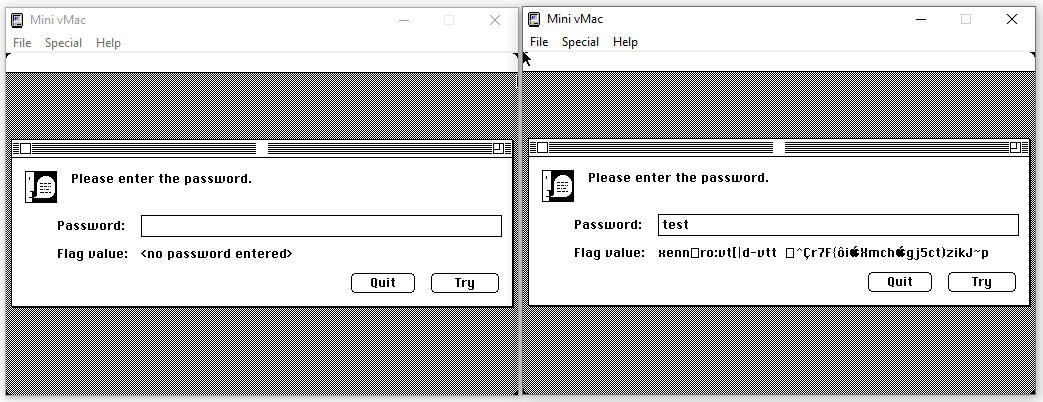
We can already tell that each character of the input password react with a unique character of the “encrypted” flag.
Also, since the hardware running this program have 16MB of RAM, a very limited disk space and a modest processor, it is unlikely that the flag is encrypted using a complex cryptographic algorithm.
The provided disassembler, Super ResEdit is a bit weird to use at first, but its core component is not that exotic:
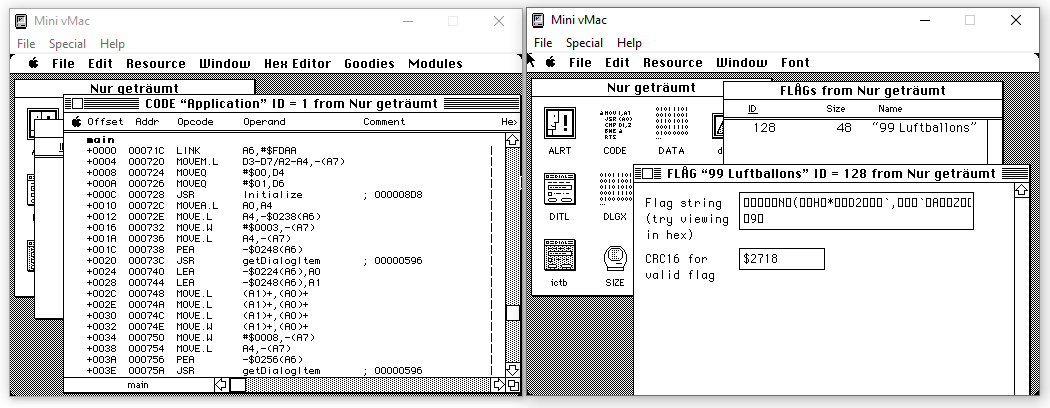
We can spot an interesting “entry” called “FLAG” in the binary (right screenshot), which hold the “encrypted” version of the flag, along with the CRC16 value $2718 that seems to correspond to the checksum of a valid flag.
Interestingly enough to notice, the “resource” section containing the encrypted flag is named 99 luftballons. This + the name of the challenge, Nur geträumt, is a reference to the German band Nena and their famous song “99 luftballons” ;).
We can even find that the creator of the challenge named himself “Nena” (right picture):
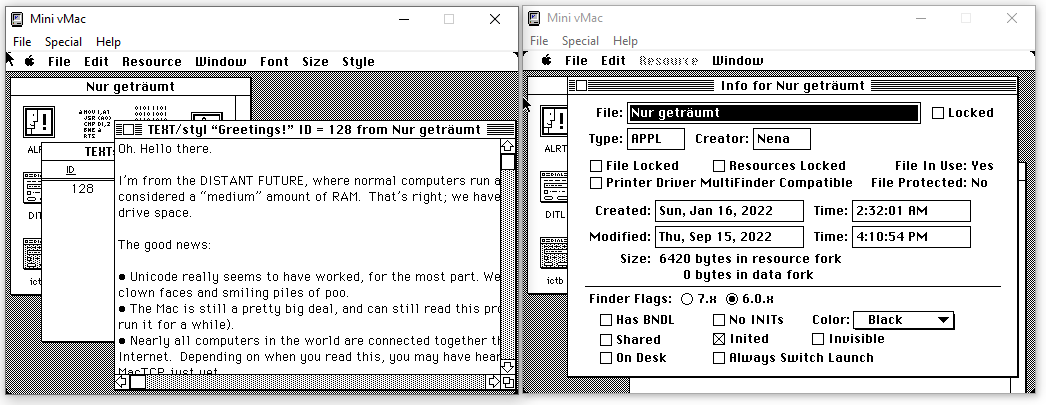
After browsing the available resources in the binary, a text called “Greetings!” can be found (left picture).
``` Oh. Hello there. I’m from the DISTANT FUTURE, where normal computers run at 2-4 GHz and 16 GB is considered a medium amount of RAM. That’s right; we have more RAM than you have hard drive space.
The good news:
- Unicode really seems to have worked, for the most part. We even have characters for clown faces and smiling piles of poo.
- The Mac is still a pretty big deal, and can still read this program (but hasn’t been able to run it for a while).
- Nearly all computers in the world are connected together through a network called the Internet. Depending on when you read this, you may have heard of it. Don’t get rid of MacTCP just yet.
The bad news:
- Nearly all computers in the world are connected together through a network called the Internet. This has made a lot of people very angry and been widely regarded as a bad move.
- Despite having 16 GB of RAM, Microsoft Word still takes up roughly half of it.
- We’re still using Microsoft Word.
Anyway, because in the future we’re stuck at home due to a worldwide pandemic (no, not the Internet, there is ANOTHER one), we had a competition for finding fun things in computer programs. I’ve hidden a flag in this program, but it’s not going to be all that easy to find just with ResEdit.
You’ll probably need to interact with the program a bit.
It will let you know when you’ve found the right flag. I’ve done you the favor of including Super ResEdit here, which has a disassembler, and I’m even nice enough to give you the debug version of the program with all the symbol names, to give you a head start (because I’m not wicked enough to make you step through it with MacsBug, but you could if you wanted).
Here’s your first hint: 1983 was a pretty good year in music.
Have fun, and enjoy the challenge! If you’re still having trouble, maybe try asking the program if it has a bit of time for you; perhaps it will sing you a song.
- Dave Riley, July 2022 ```
This very cool note gives us a few hints: first, something is definitively going on with German songs, and secondly, it seems that we have to “guess” the password. I’m not a big fan of such challenges, but we’ll see how it goes …
We can also find another hint for the flag by poking around by the plaintext strings:
The flag resource is missing.
The flag resource apears to be malformed.
You found the flag! Remove the umlaut before submiting.
So we know that the flag have an umlaut character in it.
Going straight to the flag
The binary analysis, which was a bit painful since the navigation in the disassembler is very sketchy, shows us that we are dealing with crc16-ccit and XOR operations between the encoded flag and our input.
A funny way to retrieve the flag can be found by abusing the fact that the binary shows us the decoded value of the flag, even when it’s gibberish, and more important, that a single permutation in the input string result in a single permutation in the decoded flag value.
Since we know that the flag has to end with flare-on.com, we can cheat a bit to leak a portion of the flag.
The game is to play with a random portion of the input string until we manage to display the flare-on.com string in the decoded value:
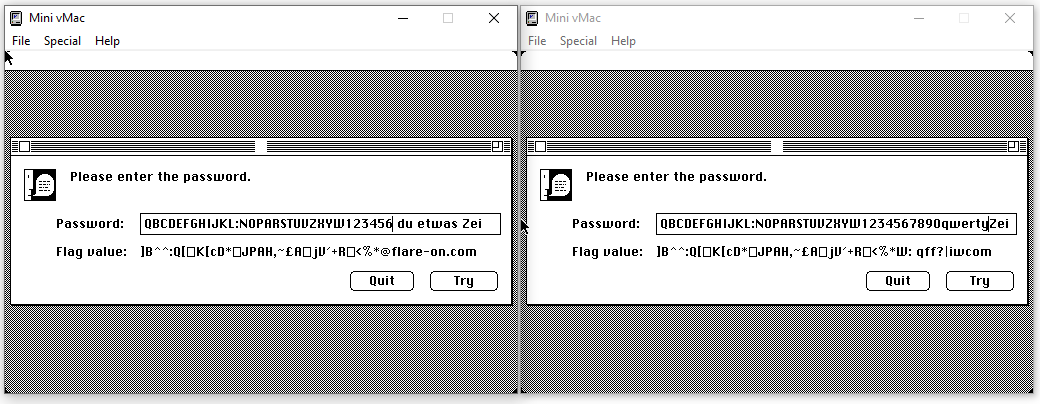
Since the input string has to be readable (including some German characters), the number of possibilities are reasonable.
Unfortunately, we can’t go further, but we still have a portion of the flag:
` du etwas Zei which translate to @flare-on.com` when at the last position of the input.
One last easy manipulation would be to rotate the position of the correct part of the input that we have to different positions. In case of a basic cyclic encoding, and only if the length of the input is smaller that the length of the decode flag, we could manage to leak another part of the flag. This theory appear to be true, and allows dumping a bit more characters of the flag:
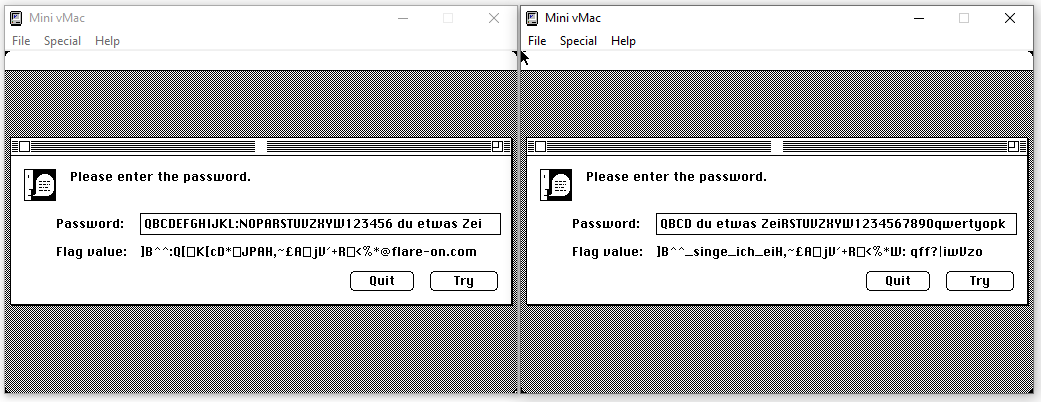
This time, ` du etwas Zei translate to _singe_ich_ei`.
Putting all the hints that we have so far allows to easily find the correct input.
The absurd amount of reference to the German band “Nena”, the “99 luftballons” section, the title of the challenge plus the string ` du etwas Zei` guides us to the lyrics of the “99 luftballons” song:
Hast du etwas Zeit für mich
Dann singe ich ein Lied für dich
Von neunundneunzig Luftballons, auf ihrem Weg zum Horizont
[...]
To no one’s great surprise, the part of the correct input we leaked is in fact a part of the first line in the lyrics of the song.
And bonus point as it contains an umlaut.
Trying with this gives us the flag (did not manage to type the umlaut in the emulator, but we can easily guess the missing letter):
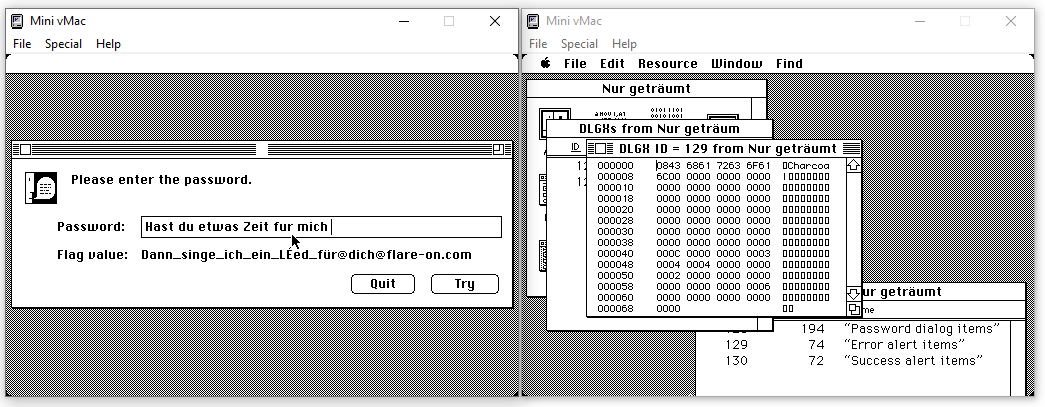
Since the descriptions and the few hints in the challenge where basically pushing me along the “guess the password” line, that’s what I did, and it worked! And it gave me a nice playlist to listen to while solving this very unusual challenge :)
Dann_singe_ich_ein_Lied_fur_dich@flare-on.com